Download from GitHub:
https://github.com/NicklasAhlberg/AutopilotTool
.Version 1.0.3.0 (2023-07-05)
– The tool has been updated to reflect the changes done to MS Graph.
– Changes to the UI
– No need to pre-define the tenant/domain name, just sign on and you are good to go
– A registered app is needed
.Version 1.0.2.6 (2022-12-14)
– It is now possible to add multiple domains to the config-file.
.Version 1.0.2.5
– It is now possible to add a default tag to the config file
.Version 1.0.2.4
– Slightly new graphical interface
– Optional: It is now possible to add a group tag!
– Use the gather logs button to get autopilot logs as a CAB file
.Version 1.0.2.3 (2021-08-17)
It is now possible to set a default domain name. Get the latest version (1.0.2.3) from GitHub and you will find “config.txt” – edit as per your need. Thanks Dylan Brown for the idea!
.Version 1.0.2.2
It is now possible to use a custom logo. Place “logo.png” in the same directory as the .exe
Recommended logo size: 210×110 px
If you have been working with Windows Autopilot you know that manual upload of the hardware hash is a repetitive and time consuming task.
This tool will make your life easier by…
- Install the necessary PowerShell modules
- Connect to the tenant (MFA is supported)
- Automatically uploading the autopilot hash to the Windows Autopilot service
- Let you know when the upload has completed (success or error)
…. directly from the device!
No more need to struggle to manually get, move and import the csv-file from another device. All you need to do is run the tool (Shift+F10 when you get to pick your keyboard layout), start Autopilot Tool and sign in to Azure with an administrative user. This works well with MFA!
Instructions
- The Autopilot Tool will require a registered app in your tenant to be allowed to run the MS Graph calls. Follow the prerequisites at the end of this blog post for guidance on how to set that up.
- Open: Config.txt and add your tenant and client (application) ids and a group tag (save and close)
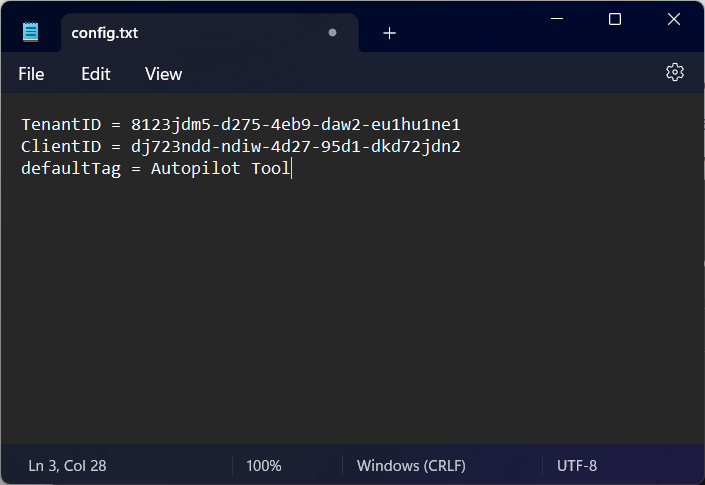
- Place: “Autopilot Tool.exe” and “config.txt” in same directory on either a USB-stick or on a network location
- Press: Shift+F10 when you are at the “pick your keyboard layout” screen
- Write: PowerShell + hit enter to start PowerShell
- Run: Install-Module MSAL.PS to install the needed PowerShell module (more info: AzureAD/MSAL.PS (github.com) )
- Navigate to “Autopilot Tool.exe”, press enter to start the tool
- Optional: add a group tag
- Click: Upload and sign in with a user with sufficient privileges
- The hash will be uploaded to the Windows Autopilot service automatically after 2-3 minutes (the tool will query the service and let you know as soon as it is ready).
Download the tool from Github:
https://github.com/NicklasAhlberg/AutoPilotTool
| Windows 10 version | Supported |
|---|---|
| 21H1 | OK |
| 20H2 | OK |
| 2004 | OK |
| 1909 | OK |
| 1903 | OK |
| All Windows 11 | OK |
Prerequisites: Register the app
We will use an Azure registered app with delegated permissions to execute our MS Graph calls against. Please note that the app itself cannot do changes beyond these permissions even if the user running the tool has more permissions, and the other way around. The next steps cover how to create the app and delegate the appropriate permissions.
- You will need either Global Administrator or Application Administrator to register the app in Azure
- Navigate to: https://portal.azure.com
- Click: Azure Active Directory
- Click: App registrations
- Click: New registration
- Name: I will use ‘Demo-Graph‘, but you may name the app differently (What about “Autopilot Tool”?)
- Supported account types: Accounts in this organizational directory only
- Redirect URI (Select a platform): Public client/native (mobile and desktop)
- Redirect URI (URL): https://login.microsoftonline.com/common/oauth2/nativeclient
- Click: Register

- Save the Application (client) ID in notepad, we will need it later
- Click: API Permissions

- Click: Microsoft Graph

- Click: Delegated permissions

- Search for and mark:
- DeviceManagementServiceConfig.ReadWrite.All
- Click: Add permissions ❗below printscreens have been reused from another post and includes more permissions than needed by the Autopilot Tool. DeviceManagementServiceConfig.ReadWrite.All is enough in our case.
- Click: Grant admin consent for…

- Click: Yes
- Make sure that the permissions have been granted accordingly

- Now navigate to https://portal.azure.com/
- Click: Azure Active Directory
- Save the Tenant and Client/application IDs in config.txt
Is the administrative user you are saying in azure or just in the local admin? Thanks
Hello,
The administrative user is an Azure identity with Intune Admin privileges or similar. Thanks for your question I have updated the info text.
Is it possible to exchange your logo for that of our company for internal use?
It might be nicer for the users. Otherwise, your tool is gigantically good. Many thanks
That is fully possible with latest version
Thanks for the feedback! 🙂
best regards
Nicklas
A handy version of this would be for a (remote) end user to run, then automatically launching the default mail client with the hash CSV file as an attachment for forwarding to IT for importing.
Hi Jörn, Thanks for reaching out. That is a good idea for a future version 👍
Regards
//Nicklas
What permissions/apps is this needing to contact? I have bypassed “microsoft intune powershell” application in my CA policies however I’m still being blocked. We require MFA AND hybrid join from global admin accounts, and despite excluding the app, these rules are still triggering on “microsoft intune powershell” despite being excluded.
Hi Jason,
The users running the tool should be “Intune admin” or similar. If your CA requires the device to be hybrid joined it will not work to you run it on a device before it has ben provisioned by Windows Autopilot, as the device is not hybrid joined at that point.
//Nicklas
Tool was working perfectly for 2 years but now we are getting “Unhandled exception has occurred in a component in your application. If you click Continue, the application will ignore this error and attempt to continue”. If we click continue it won’t do anything. Then running tool again > same error.
Hi, thanks for reaching out!
The tool has been updated and is found here: https://www.rockenroll.tech/2020/11/09/autopilot-tool-upload-hw-hash-with-a-user-interface/
Best regards
Nicklas
Hello,
When clicking on “upload” Loading sign-in prompt please wait a long time in de background and in front only a white screen not showing the Microsoft login.
Do you have an idea?
I make use of the config file
Hi, thanks for reaching out!
It sounds like the sign-in prompt/window doesn’t render correctly. Have you tried to close the white image/screen and click Upload again?
Let me know how it goes.
//Nicklas
Hej Nicklas,
I have registered the app with Granted permissions.
Now, when i want to test the App, I get an error: “We couldn’t create the data directory” , “Microsoft Edge can’t read and write to its data directory”
-I’m running the app as Admin
-On a no Local Admin Device
-Already onboarded to WAP
-Managed by Intune
-Hybrid joined
Do you know if this scenario is even possible?
P.S. New Device is coming in 2h so i will also try OOB scenario
Thank you!
All Best,
Marko
Hi Marko,
* Did you fully follow the steps to register the app and apply correct API-permissions?
* I recommend that you run the tool on a device which has not been uploaded to the Windows Autopilot service yet.
//Nicklas
I managed to get the new version working on our windows 11 machines. But we had an issue that the Get-MSALtoken command was not found and we had to install the module.
Install-Module -Name MSAL.PS
once installed the applicatons worked fine. Any chance to get it to install it automatically if not found in future versions please.
Hi,
Thanks for the feedback.
As for now step 6 in the manual covers how to install the module. I am working on a new version which will not need the module at all, hope to have it done early/mid Q4.
//Nicklas
The “Autopilot Tool.exe” is not in the github repository. Did you stop supporting this tool? Thanks for your effort anyway.
Hi Alfonso!
The tool is downloaded from the releases section (found to the right) over at Github.
br,
Nicklas
hi,
tool is great and wonder if there is a chance to get the source code.
kr
Hi, this is probably the part of the code you are looking for:
# Get hash info from local device
$autopilotHashDeviceHashData = (Get-WmiObject -Namespace “root/cimv2/mdm/dmmap” -Class “MDM_DevDetail_Ext01” -Filter “InstanceID=’Ext’ AND ParentID=’./DevDetail'” -Verbose:$false).DeviceHardwareData
$autopilotHashSerialNumber = (Get-WmiObject -Class “Win32_BIOS” -Verbose:$false).SerialNumber
$autopilotHashProductKey = (Get-WmiObject -Class “SoftwareLicensingService” -Verbose:$false).OA3xOriginalProductKey
if ($textbox1.Text) # Add autopilot tag to json body (if needed)
{
$autopilotHashGroupTag = $textbox1.Text
}
# Create json body based upon local device info and autopilot tag
$autopilotHashbody = @”
{
“importedWindowsAutopilotDeviceIdentities”: [
{
“groupTag”: “$autopilotHashGroupTag”,
“serialNumber”: “$autopilotHashSerialNumber”,
“hardwareIdentifier”: “$autopilotHashDeviceHashData”
}
]
}
“@
$autopilotHashData = Invoke-RestMethod -Headers @{ Authorization = “Bearer $($token)” } -Uri ‘https://graph.microsoft.com/beta/deviceManagement/importedWindowsAutopilotDeviceIdentities/import’ -Method ‘POST’ -Body $autopilotHashbody -ContentType ‘application/json’